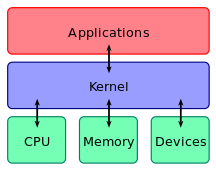
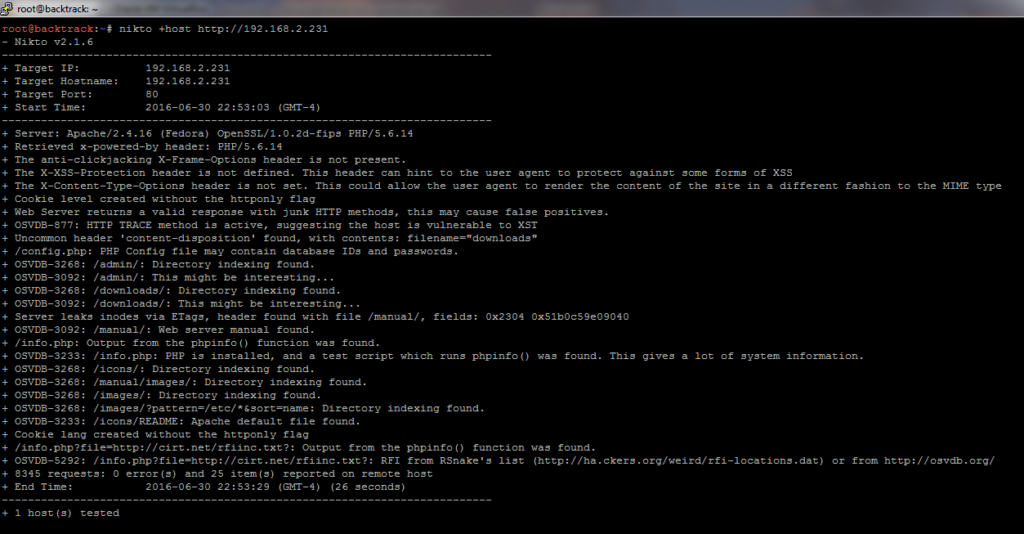
Python is a great programming language to build web applications with. Not only is the entry bar lower than other languages, there’s a wide variety of web frameworks to choose from (e.g. Flask, Django).
My personal favorite is Flask. Flask is easy to use and has the ability to scale out (i.e. Blueprints). When building my personal website, I wanted to keep things simple. The design is minimal and serves the intended purpose. With the endpoints however, I wanted to be more creative. Currently, there are two endpoints: /skills and /education. Both /skills and /education accept only two HTTP methods: GET and OPTIONS. Later on, I’m going to create some cooler endpoints that integrate with other Python libraries. However, for now, I think querying endpoints for data is just as cool.
card.mcclunetechnologies.net is my personal website. The site is essentially my virtual business card. I want to have endpoints that are under-the-radar and return more information about myself. Right now, you can query /skills and /education by navigating to the endpoints directly. You can also send a GET request using a tool like curl.
Both endpoints return JSON responses. When querying an endpoint like /skills, Python will open a connection to a remote MySQL database and fetch all information within the appropriate table. As the OPTIONS method describes, /skills will return the following:
user@debian:~$ curl -s -XOPTIONS https://card.mcclunetechnologies.net/skills
Supported Methods for /skills: GET
Provides the following information: skill_name (string), skill_description (string), years_of_experience (integer), and comfort_level (string; can either be low, medium, or high)
Sending a GET request to /skills will return the MySQL fetchall() response dumped into JSON:
user@debian:~$ curl -s -XGET https://card.mcclunetechnologies.net/skills
[
[
"Active Directory",
"Active Directory (AD) is a directory service developed by Microsoft for Windows domain networks. It is included in most Windows Server operating systems as a set of processes and services. Initially, Active Directory was only in charge of centralized domain management. However, Active Directory became an umbrella title for a broad range of directory-based identity-related services.",
7,
"medium"
],
[
"Ansible",
"Ansible is an open-source software provisioning, configuration management, and application-deployment tool enabling infrastructure as code. It runs on many Unix-like systems, and can configure both Unix-like systems as well as Microsoft Windows.",
2,
"medium"
],
[
"Apache CloudStack",
"CloudStack is open-source cloud computing software for creating, managing, and deploying infrastructure cloud services.",
3,
"medium"
],
[
"Bash",
"Bash is a Unix shell and command language written by Brian Fox for the GNU Project as a free software replacement for the Bourne shell. First released in 1989, it has been used as the default login shell for most Linux distributions and all releases of Apple's macOS prior to macOS Catalina.",
4,
"medium"
],
[
"Cisco IOS",
"Cisco Internetwork Operating System (IOS) is a family of network operating systems used on many Cisco Systems routers and current Cisco network switches.",
7,
"medium"
],
[
"Git",
"Git is a distributed version-control system for tracking changes in any set of files, originally designed for coordinating work among programmers cooperating on source code during software development.",
4,
"medium"
],
[
"Linux",
"Linux is a family of open-source Unix-like operating systems based on the Linux kernel, an operating system kernel first released on September 17, 1991, by Linus Torvalds. Linux is typically packaged in a Linux distribution.",
7,
"high"
],
[
"Nagios",
"Nagios Core, formerly known as Nagios, is a free and open-source computer-software application that monitors systems, networks and infrastructure.",
6,
"medium"
],
[
"Python",
"Python is an interpreted, high-level and general-purpose programming language. Python's design philosophy emphasizes code readability with its notable use of significant whitespace. Its language constructs and object-oriented approach aim to help programmers write clear, logical code for small and large-scale projects.",
2,
"medium"
],
[
"Technical Support",
"Technical support (often shortened to tech support) refers to services that entities provide to users of technology products or services. In general, technical support provides help regarding specific problems with a product or service, rather than providing training, provision or customization of the product, or other support services.",
7,
"high"
]
Here’s the /skills endpoint within my Flask view:
@about.route("/skills", methods=["GET", "OPTIONS"])
def skills():
if request.method == 'GET':
conn = mysqlConn()
skillsCursor = conn.cursor()
skillsCursor.execute("SELECT * FROM skills")
skillsInfo = skillsCursor.fetchall()
skillsCursor.close()
conn.close()
return json.dumps(skillsInfo, indent=4)
elif request.method == 'OPTIONS':
return skillsOptions
/skills and /education don’t have filtering capabilities, however, you can use a tool like jq to achieve similar results. One example is filtering just the skill names:
user@debian:~$ curl -s -XGET https://card.mcclunetechnologies.net/skills | jq .[][0]"Active Directory""Ansible""Apache CloudStack""Bash""Cisco IOS""Git""Linux""Nagios""Python""Technical Support"