The SANS Institute created a fun hacking challenge for this year’s Holiday Hack. Everything from packet analysis to web exploits were included. The packet capture showed how the devious Gnomes were taking pictures of children and receiving them through DNS queries. To be honest, I didn’t think this type of malicious intent was possible (especially through DNS queries). Here’s what I’m talking about:
The following is the packet capture with the image encoded in Base64. Using tools such as Burp Suite and the Linux base64 utilities will help uncover the image secretly hiding within.
Here is the packet capture with the UDP stream of DNS requests being sent to the SuperGnomes. SuperGnomes were the super computers that housed the data collected from the individual GIYH’s.
After exporting the UDP stream to a RAW format, I then used foremost (a tool contained within Kali Linux) to carve out the picture. The JPG was found after decoding the base64 encoding within the capture.
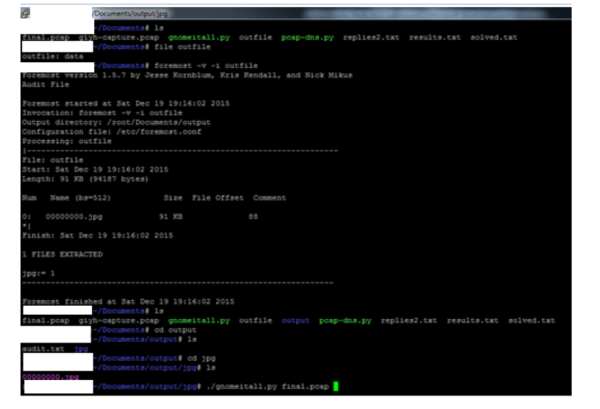
Here is 00000000.jpg, which was the file being sent over the Gnome’s command and control channel:

The packet capture challenge was just one of many activities in this year’s Holiday Hack. For the sake of brevity, I am only going to post this one. However, if you are interested in doing this challenge next year, please check out the website at https://holidayhackchallenge.com or by going to https://sans.org.
(Originally posted on January 10th, 2016. Updated on December 29th, 2020)